Network Difficulty, Share Difficulty and Hash Functions
What is the Bitcoin network difficulty and how are mining share difficulties calculated?
This article is meant to serve as a guide to understanding how crypto mining works from a miner’s perspective.
It is impossible to explain some of these concepts without using math functions, so bear with us. We tried to simplify the concepts where possible. Crypto Mining: Network Difficulty, Share Difficulty and Hash Functions.
Network Difficulty
Network Difficulty describes the base difficulty, or the minimum difficulty the underlying blockchain will accept as a valid block. Effectively this is how hard it is for a miner to find a block (i.e. how hard a math problem miners need to solve). The higher the Network Difficulty the harder it is to find a block.
Network Target
From an outside perspective the network operates on Network Difficulty but under the hood it is being calculated on the inverse, the Network Target.
Network Target = 1 / Network DifficultyThe higher the Network Target, the easier it is to find a valid block (inverse of Network Difficulty).
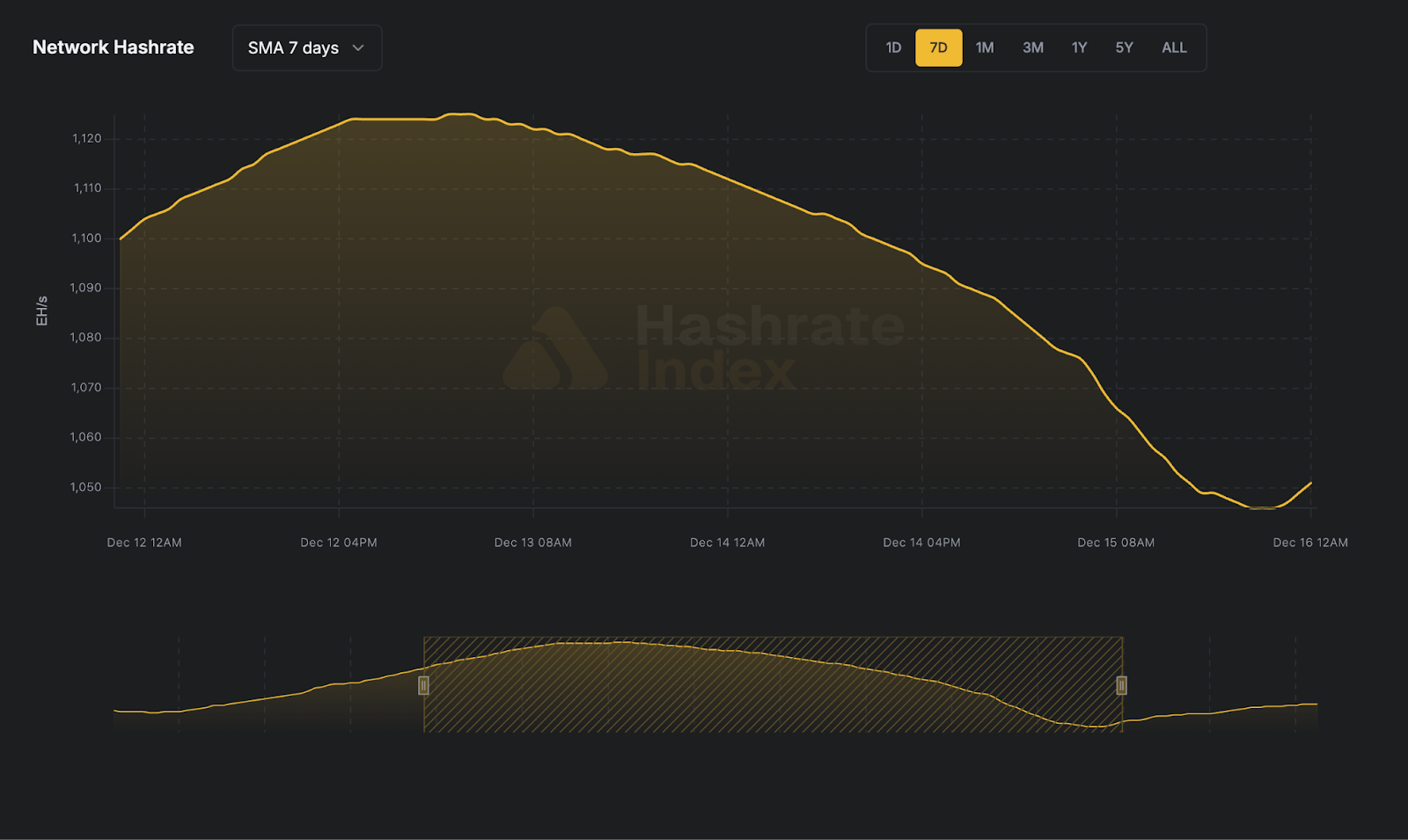
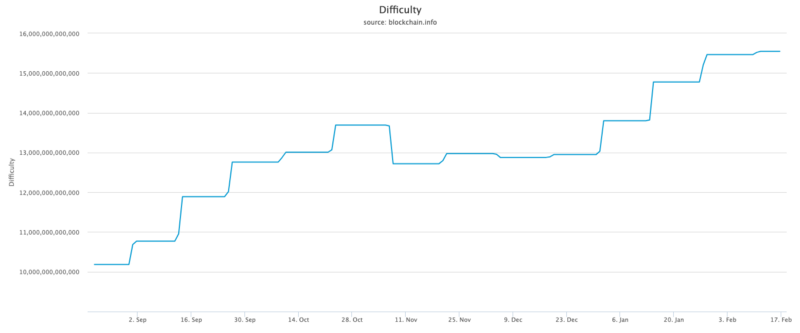
Difficulty over Time
Networks have a Difficulty Adjustment Algorithm (DAA), which essentially is a built-in hashrate measurement that adjusts the difficulty. Taking BTC blockchain as an example, the difficulty adjustment comes every 2,016 blocks (roughly 2 weeks). The adjusted Network Difficulty is calculated as the network’s average hash rate from the previous period. Based on that average, the new Network Difficulty is set such that, if that average hash rate is maintained, the network will find a new block every 600 seconds (144 blocks per day).
The easy way to look at it is, if more people are competing to solve a math problem, the problem needs to get more difficult if you want the time it takes to solve the problem to stay constant.
The Bitcoin Network Difficulty over time can be found here.
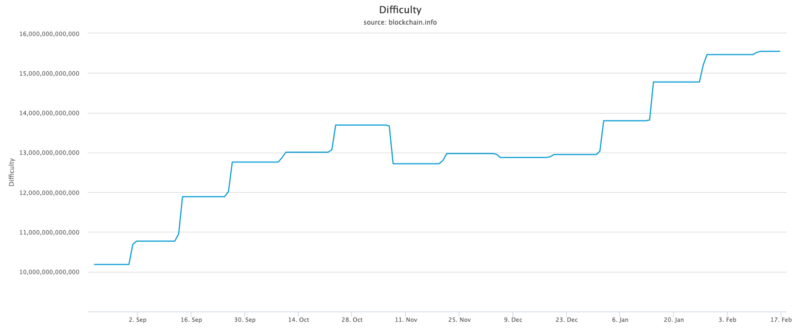
Many other coins have implemented more frequent difficulty adjustments. A common DAA for Equihash coins like ZEC and ZEN is DigiShield v3 which adjusts difficulty after every block.
Share Difficulty
ASICs produce billions of hashes per second. For example the new Bitmain S17+ produces 73 Terahashes per second. Mining Pools can’t collect and check all of these hashes from their miners.
So Mining Pools set a target Share Time. This could be something like 5 seconds, which means that on average Mining Pools want miners to submit a share to them every 5 seconds.
To make this possible, Mining Pools set a Share Difficulty for every miner. Based on your hashrate, Mining Pools set how hard it is to submit a share to them. The higher the hashrate, the higher the Share Difficulty. When miners are grinding through hashes, they will eventually find a hash that meets the target Share Difficulty, then they send it to their Mining Pool.
In a PPS payment method, miners get rewarded by a mining pool for shares they submit. The shares they submit have different values based on how difficult it was to find the share. Miners get credited based on the set Share Difficulty from the Mining Pool not the actual share difficulty.
Let’s run through an example of this.
Mining Example
- Let’s say you are mining at 50 TH/s and the Mining Pool sets your Share Difficulty at 1,000,000. You get credited by the pool for all shares that are above 1,000,000.
- If you then increase your hashrate to 100 TH/s, the pool will change your Share Difficulty so that you aren’t submitting shares too quickly. If your pool increases your Share Difficulty to 2,000,000, then you will submit shares at the same speed you previously were, but you will receive two times as much revenue from the pool for the shares you do submit.
- You end up making twice as much revenue (which mirrors your increase in hashrate).
Share Target
Like the Network Difficulty, Share Difficulty can also be converted to a Share Target by taking the inverse.
Share Target = 1 / Share Difficulty
Hashing Function
A hash is the output of a hash function. Hashrate is the speed at which a computer (ASIC/GPU/CPU) is completing an operation in the cryptocurrency’s code. Therefore, the amount of hashes are measured in hashes per second.
At its base you can think of crypto mining as solving some function represented by:
f(x) = yWhere:
- f = Hash Function (i.e. an equation -> such as SHA-256)
- x = Block Header (i.e. some random number)
- y = Result of the Hash Function applied on the Block Header
Hash Function (f)
You can think of the Hash Function such as SHA-256 (f) as a very complex equation that will input the Block Header (x) in some way to create a hash result (y).
The key here is that the formula (f) is too complex to solve using algebra. The only way this can be solved is by using brute-force, guess & check. Miners constantly change the block header (x) in the equation until the result (y) is acceptable.
This is known as a trapdoor function; a one-way function that makes it impossible to know which x value will give you y without brute-forcing it. This is what ASICs are doing. Just guess & checking x values until they find a y outcome that is acceptable.
Block Header (x)
The way miners change x is a bit more nuanced. The Block Header is a large string of numbers and is function of a few different inputs. We included some of the main ones below but it is not exhaustive.
~Block Header = Block Height + Block Version + Previous Difficulty + Nonce
The key is that all of the variables are set, except for the Nonce. The Nonce is what miners are constantly changing to change the Block Header (x).
Result of the Hash Function (y)
This is just the outcome of the function (f) using an input (x). But it is crucial for mining.
The result (y) is what is used to determine if a share will be accepted by the pool, and if the share can create a valid block.
Mining Example
Using SHA-256 (f) as an example, let’s say a Mining Pool sets a Share Difficulty of 1,000,000 for the Miner. This results in a Share Target of ( 1 / 1,000,000) = 0.0000010000
The miner (ASIC) is going to start guessing numbers until they reach the target outcome. So they will continue to guess new Block Headers (x) in the function (f).
- f(x) = y
- SHA-256(block_header_guess1) = 0000241241
- SHA-256(block_header_guess2) = 0000041241
- SHA-256(block_header_guess3) = 0000001241
The **block_header_guess3 **(x) resulted in a hash (y) that was lower than the Share Target. So it is accepted by the pool as valid and the miner gets paid for that share.
Now let’s assume the miner keeps mining. The Network Difficulty is 100,000,000 which results in a Network Target of (1 / 100,000,000) = 0.0000000100
- SHA-256(block_header_guess3) = 0000001241
- SHA-256(block_header_guess4) = 0000000241
- SHA-256(block_header_guess5) = 0000000041
The block_header_guess5 (x) resulted in a hash (y) that was lower than the Network Target. So it is used by the pool to submit a valid block to the network and get the block reward!
Hashrate Index Newsletter
Join the newsletter to receive the latest updates in your inbox.